USCG Season IV Pwn Write-Ups
For the USCG Combine, this weeks focus was pwn! Here are some writeups for the challenges that were given for the combine.
Binary Blast
Challenge Description
Ready for a blast from the past? Navigate the MIPS landscape and watch out for those sneaky format strings. Beware of fake flags—only the real one will do!
This challenge makes it fairly clear that it is a format string pwn, but instead of being on an architecture we may be used to, it is on MIPS.
Initial Analysis
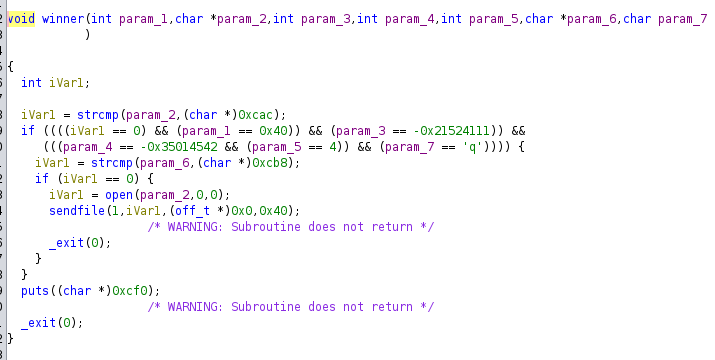
winner function, which appears to open a file assuming we can call it with the correct parameters.
Our plan to solve this seems pretty straightforward, as we just need to abuse the format string vulnerability in order to call the winner function with specfic parameters.
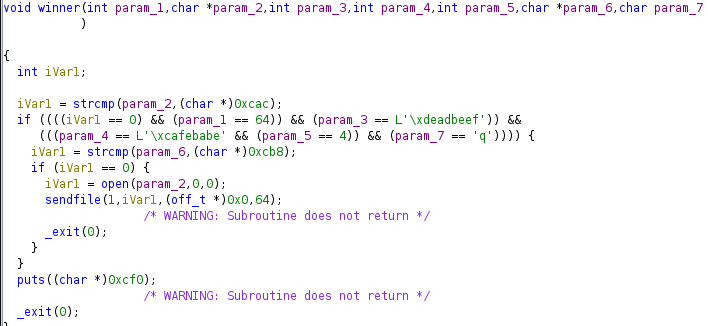
Changing the types, we can get something that becomes much more clear. For format strings, one thing we can try doing is to overwrite the _exit function with something else (such as main), which will allow us to execute multiple payloads, since it will essentially just loop back to main instead of exit.